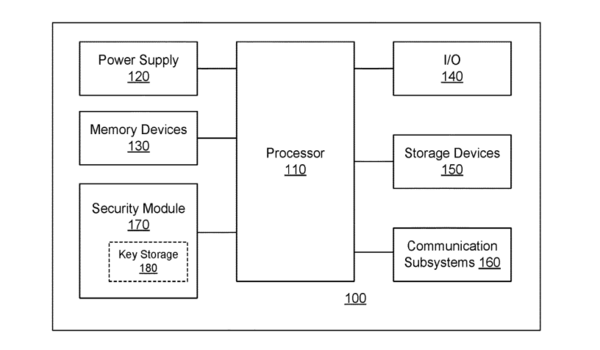
Quantum-augmentable hybrid encryption system and method - Ted Rogers School of Management - Toronto Metropolitan University
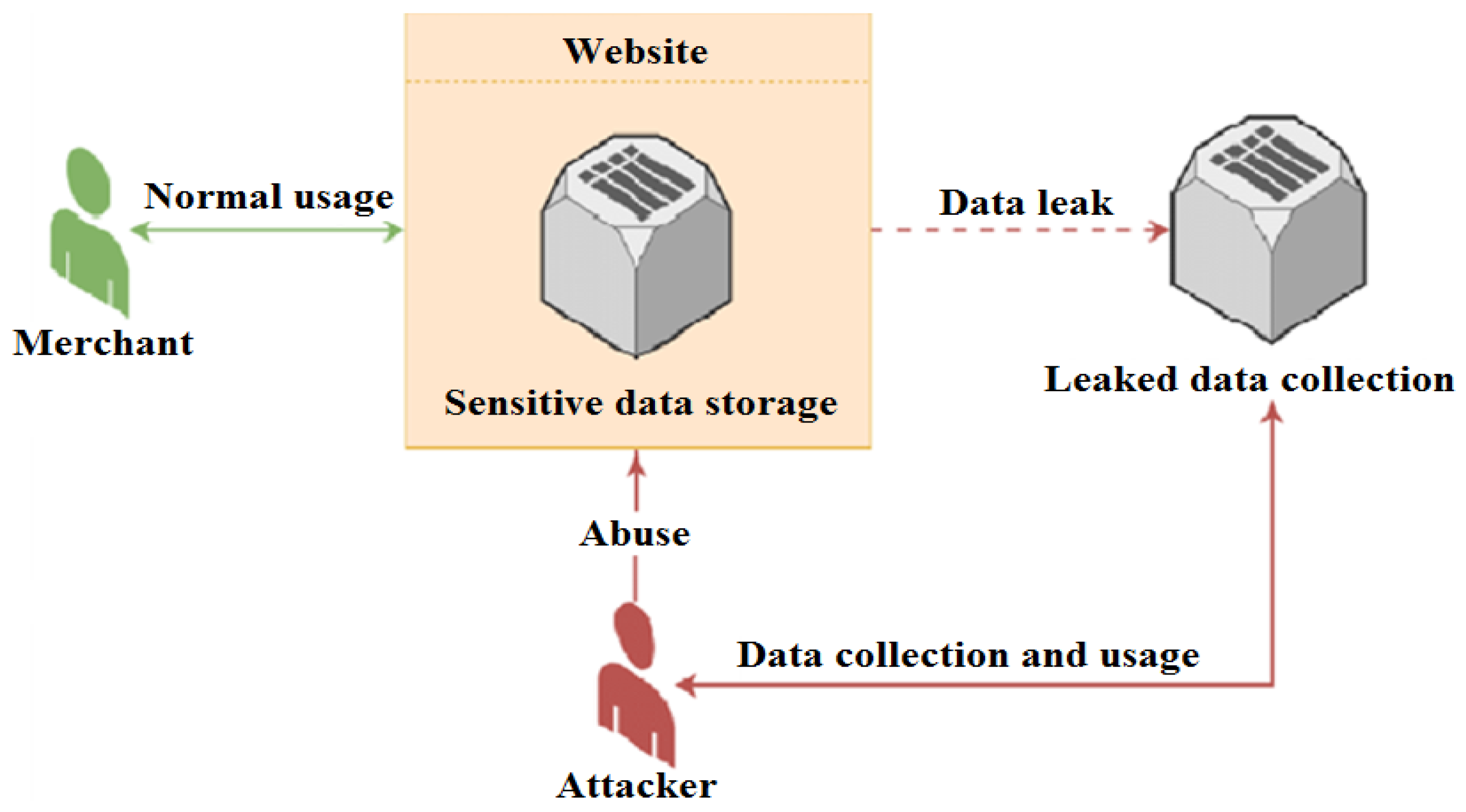
Future Internet | Free Full-Text | Applying Detection Leakage on Hybrid Cryptography to Secure Transaction Information in E-Commerce Apps

A Hybrid Crypto System based on a new Circle- Symmetric key Algorithm and RSA with CRT Asymmetric key Algorithm for E-commerce Applications | Semantic Scholar

A Comparative Study of Various Traditional and Hybrid Cryptography Algorithm Models for Data Security | SpringerLink

A Novel Hybrid Encryption Method to Secure Healthcare Data in IoT-enabled Healthcare Infrastructure - ScienceDirect
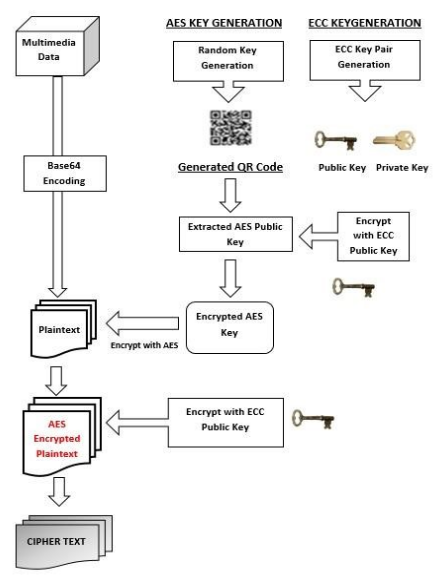
Hybrid-Cryptography | Implementation of a system capable of encryption and decryption of multimedia data (Text, Images, Videos, Audio etc.) using a hybrid model based on the amalgamation of symmetric encryption techniques such

Hybrid Cryptography Model based on Authentication, Integrity & Privacy: Kapoor, Vivek, Bhat, Saurabh: 9786202010085: Amazon.com: Books